How to Protect from SQL Injection Attack? Top 5 Ways
Learning how to protect from SQL injection attacks is very easy for users by executing a few tasks like filtration of database inputs, restricting database code and access, updating SQL DB applications, verifying communication & networks, minimizing account privileges, and relying on advanced solutions. This way, users can not only predict but also prevent against SQL injection attacks in cyber security at any time.
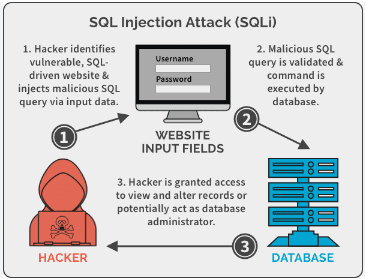
However, before we proceed further, we must understand what an SQL Injection Attack means for real. So, in layman’s language, an SQL injection attacker injects a malicious code into the database of the victim. This code bypasses the security measures & allows the attacker to view or modify the database values.
Thus, we have a few ways to learn how to prevent SQL attacks like these without going through so much trouble & technicalities. However, first, users need to verify if their database is vulnerable to the SQL injection attack or not.
How to Prevent SQL Injection Attacks in Cyber Security by Identifying Threats?
Now, the very first task that users need to focus is on the identification of threats. It is of utmost significance for a user to find out if a database is really vulnerable to SQL injection threats or not. Therefore, a user must undergo some processes to check it out.
We are aware that programmers & DBAs do their best to protect their DBs from all such threats. However, developers who work on a particular app or website using SQL platforms are the major targets of these attackers. Developer’s mistakes might be known as bugs but SQL attackers view these as loopholes to attack. These small loopholes sometimes get away from security practices & then are open to get sabotaged.
Thus, we have two major ways to identify if a database is vulnerable & requires some SQL Server security best practices or not. These two ways are:
- SQL Injection Vulnerabilities Test
- Advanced SQLi Detection Methods
Test SQL Vulnerabilities & Learn How to Prevent SQL Injection
Now, the very first step to find out the vulnerable database is to run a test for the same. These tests include VAPT or vulnerability assessment & penetration tests. Here, an engineer tries to find the loopholes with an in-depth analysis of the database. Then the engineer penetrates a database just like an attacker. After the complete testing, the report shows what & how many vulnerabilities were found. Along with that, the report shows how deep an attacker can get into & damage.
All of this happens with the help of SQL queries, tools, & other programs. Here, some minor errors can be fixed in the sport. Whereas, some need more time to rectify the chain of errors going on for too long. Then they need to learn how to protect themselves from SQL injection attacks using safety measures. If users are unable to find out the vulnerabilities this way, they can take help from the upcoming SQLi detection methods.
SQL Injection Attack Detect Methods
Users can get help from several other SQL injection (SQLi) detection ways. Cyber security specialists & open-source developers have now faced several solutions that can help detect injection attacks. These solutions are NoSQLMap, WhiteWndow, Leviathan, Tryant-SQL, BBQSQL, etc.
These solutions are specially designed by their respective developers to identify the most common as well as unique kinds of SQL loopholes. Also, it saves human error & time resources for finding the vulnerabilities which can take plenty of days in some cases.
How to Protect from SQL Injection Attack with Top 5 Methods?
Generally, there are some practices that in the early days, users preferred to safeguard their databases from attackers. As time passed, global users relied on these practices with technological upgrades on a huge scale.
The significance of these methods can be analyzed by the fact that they help users prevent all sorts of SQL injection attacks that hold the capability of destroying the entire database. These 5 methods to :
- Database Filtering
- Code Restriction in Database
- Access Restriction in Database
- Updating Database Applications
- Communications & Networks Monitoring
- Advanced Method to Prevent Against SQLi
Also Read: How to Do User Mapping in SQL Server Database Easily
#1 How to Prevent SQL Injection Attack with Database Filtering
Some users might think this is a very basic solution and it does not work. Well, this is not true. However, the database input filtration method does not guarantee safety from the SQLi attacks. Still, it does help users to identify and eliminate the vulnerable data inputs at the very root. Denying the extended URLs, & repairing the corrupted or damaged data files is a huge benefit for users.
Repair Damaged Data Files to Learn How to Prevent from SQL Injection Attack
Data sanitization & repairing of the damaged data files is one of the most crucial aspects of database filtering.
SQL injection (SQLi) attacks can deeply exploit web interfaces by injecting SQL code, potentially compromising databases to a great extent. To prevent this, users have to encounter command interpretation by sanitizing the data.
Let’s understand this with the help of an example. In any of the login attempt, an attacker might use a string like ‘password’ or 1=1, which, if not sanitized, holds the ability to manipulate the query to grant access regardless of the password validity. SQL sanitization libraries, such as mysqli_real_escape_string() in MySQL, prevent this by converting inputs to harmless strings. Another method, typecasting, restricts input to expected data types, like (int)$_POST[“id”], but it’s less versatile. Programmers must stay updated on best practices for their specific language.
Also, trusting the most reliable SQL Database Recovery Tool is also a great option for users to learn how to prevent against SQL injection attacks in cyber security.
Deny Extended URLs
Attackers often use extended URLs on a website to find out if they can target that particular website or not. Understanding this with the help of an example is even more easy.
Let’s say that an attacker searches the following query on a web browser for a domain abc-limited.com
http://www.abc-limited.com/Search.php?product="<SCRIPT>alert(‘Hello…’) </SCRIPT>"
Now, the database that does not state user inputs for verifying the javascript tags & HTML, this extended URL comes up with the following output for the attacker:
Product “<SCRIPT>alert(„Hello…‟) </SCRIPT>” not found…
Well, this reply from the browser gives a strong hint to the attacker that the database is vulnerable enough to get further penetrated. Therefore denying the extended URLs, can easily eliminate this entire issue.
#2 Code Restriction in SQL Server Database
A zero-day vulnerability is something that a database is not prepared for at all. These are the most dangerous vulnerabilities as no counter-action is available for the victim. Credentials compromises, insider threats, & much more are present here that can effectively trouble users.
Enforce Prepared Statements And Parameterization – To segregate the user input & SQL code, we have to execute the prepare statement & parameterization. Any SQL statement is made with placeholders for the user input> Now, the user input is provided as separate parameters. This helps prevent the user input from being interpreted as code by the database server which increases security.
Whitelist User Inputs – When we limit the characters for an input query, there is very little chance for the attackers or insider threats to put long queries to gather information. To learn how to prevent from SQL injection attacks, this is one of the most widely used tactics by SQL experts across the globe.
Reduce Available Functionality – This concept ensures that the DBAs assign only the bare minimum permissions to the users for a specific task. Here, to learn how to prevent SQL injection attacks, the goal is to minimize the possibility of users exploiting their authorization for unnecessary tasks.
Trusting Stored Procedures- Whenever the stored procedure is generated, the SQL Server cross-examines the code, which helps the server execute SPs with several parameters without recompiling. For better database validation & access control, stored procedures are something users should rely upon.
#3 Access Restriction in the SQL Database to Learn How to Protect from SQL Injection Attack
Every day, the most common vulnerability that VAPT engineers find in SQLi cases, is compromised user credentials. This is the most basic thing that every database user should take care of. In order to downgrade the impact of such attacks, we need to consider the following decisions:
- Putting a limitation on external access with a firewall.
- Both virtual & physical firewalls are helpful in this case.
- Avoiding shared account usage & encryption can reduce the damage from attacks.
- Make strict access policies & limit the read access.
- For minor error messages, database functions, & tables, we should limit user access.
- There should be unique logins for the distinct assets.
#4 Communications & Networks Monitoring to Prevent SQLi Attack
To learn how to protect from SQL injection attack, users must pay attention to communications & networks. It should be a regular task to monitor all the statements related to the third-party applications & must be communicated from time to time.
Constant network monitoring also helps to prevent from SQL injection attacks that nowadays are trending. It helps in multiple activities like:
- Identifying Suspicious Events.
- Early Warning System
- Enhanced Data Forensics
#5 Protect from SQL Injection Attack by Updating Database Applications?
We can easily find SQL injection vulnerabilities in several third-party applications. To safeguard the database from such issues, users need to be updated on these vulnerabilities and apply the corresponding patches as soon as possible. It is a hassle-free way to know how to prevent SQL attacks in cyber security with ease.
This includes the updation for almost every part of a web application, from the database software to the web server itself. Nowadays, users have the availability of patch management solutions to automate the entire process of updation.
Also Read: SQL Server User Roles & Permissions in Depth Understanding
Wrapping Up
Now, after going through the detailed process, users must be aware of how to protect from SQL injection attack without letting any part of database suffer from damage. With the right solutions, it is not difficult for any user to learn how to prevent from SQL injection attacks with minimalistic knowledge of SQL technicalities. Moreover, if users pay more attention to the VAPT part, they can execute quick actions to prevent such threats from taking the face of a big tragedy.