How to Do User Mapping in SQL Server? Know the Detailed Guide

Summary: In this post, we will discuss one such common query on the “How to do user mapping in SQL Server ”. Along with that, we will discuss the concept, importance, and process of mapping users to logins. If you are looking for the same, then read this blog post till the end!
In SQL Server, user mapping is a significant part of database management. It allows users to control access to the SQL database along with several other integral benefits. However, each user needs to have a thorough understanding of user mapping in SQL Server. Read this complete blog to understand all the concepts in detail.
What is User Mapping in SQL Server?
SQL user mapping is the process of establishing a connection mapping between a user identity in one system or organization and a user identity in another. It is helpful when two system users need to communicate and exchange data but have separate user accounts or authentication procedures.
Learn How to Do User Mapping in SQL Server with these Prerequisites:
The Two-Step Authentication for mapping user to SQL Server database:
- Server Login: This is the first server login for the user. It makes use of credentials, such as Windows credentials, certificates, and usernames and passwords.
- Database Users: To access particular sections (databases), users must first obtain additional authorization after entering the building (server). Database users with the appropriate rights can now intervene in this situation.
Also Read: Learn SQL Server Security Best Practices without any hassle.
In the next section, we’ll discuss the process of user mapping in SQL Server. Let’s have a look at them:
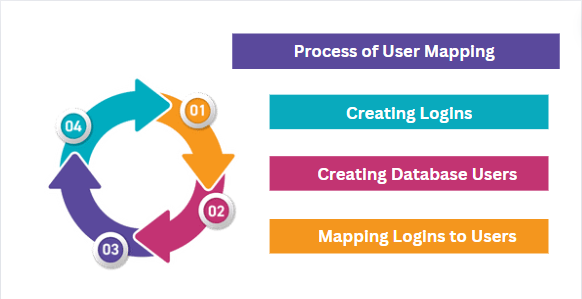
Process of User Mapping in SQL Server
As we said earlier, SQL Server user mapping is a process of establishing a connection between a server login and a database user. This mapping process makes sure that users can only access specific databases with the right permissions.
- Creating Logins: The first step involves creating a login using the Transact-SQL commands or a T-SQL command (CREATE LOGIN) or SQL Server Management Studio (SSMS). During the login creation process, the authentication mode (Windows Authentication or SQL Server Authentication) is selected and login credentials are entered.
- Creating Database Users: Once logins are successfully created, the database users are created within individual databases using CREATE USER commands. Database security is linked to server security by the usage of matching logins for database users.
- Mapping Logins to Users: The final step is the SQL Server user mapping logins to users. You can use ALTER USER or ALTER LOGIN statements to achieve this. With this user can specify the login and the associated database user.
By following the above-mentioned steps, users can easily map users to databases in SQL Server, enabling secure and controlled access to data.
How to Check User Mapping in SQL Server?
In this section, we will discuss two methods to check user mapping in SQL Server. The first one is the SQL Server Management Studio (SSMS) and the second method is the Transact-SQL (T-SQL) command. By following these methods you can easily resolve the “How to do user mapping in SQL Server” user query.
Method 1: Using SQL Server Management Studio (SSMS)
Follow the following procedure to accomplish the task effortlessly:
1. First, open your system’s SQL Server management studio SSMS and connect to your SQL Server instance.
2. After this, go to the “database” where you want to check user mapping.
3. Then, expand the “Security” folder, and expand the “Users” folder within the selected database.
4. Now, right-click on the user for whom you want to check the mapping and choose “Properties.”
5. Go to the “User Mapping” page under the user properties wizard. Now, you will see a list of the SQL databases in which the user is mapped and their corresponding roles and permissions within each database.
Method 2: Using T-SQL Command
You can use the T-SQL command to check the user mapping in SQL Server. Here are the steps for a T-SQL query to retrieve user mapping information and resolve the “How to do user mapping in SQL Server” query:
If you want information in bulk then you can use this command.
USE [YourDatabase];
SELECT
dp.name AS DatabaseUserName,
sp.name AS LoginName
FROM
sys.database_principals dp
JOIN
sys.server_principals sp ON dp.sid = sp.sid
WHERE
dp.type IN (‘S’, ‘U’, ‘G’)
AND dp.name <> ‘guest’
ORDER BY
dp.name;
If you want information on a single server login, you should run the following command.
DECLARE @login sysname = N’your_login_name’;
SELECT
db_name(d.database_id) AS DatabaseName,
u.name AS Username,
u.default_schema_name AS DefaultSchema,
STUFF((
SELECT ‘,’ + r.name
FROM d.sys.database_role_members AS rm
INNER JOIN d.sys.database_principals AS r ON rm.member_sid = r.sid
FOR XML PATH(”), TYPE
), 1, 1, ”) AS Roles
FROM sys.server_principals AS sp
INNER JOIN sys.logins AS l ON sp.sid = l.sid
INNER JOIN sys.databases AS d ON d.sid = sp.sid
LEFT OUTER JOIN d.sys.database_principals AS u ON l.sid = u.sid
WHERE sp.name = @login;
In the upcoming section, we are going to discuss the best practices to resolve the “How to do user mapping in SQL Server” query. Whether you are a tech-savvy or novice user this will help you a lot to learn about user mapping in SQL Server.
Best Practices for SQL Server List Logins and User Mappings
In this part, we’ll look at some SQL Server user mapping recommended practices. Let’s take them one by one:
- Grant Appropriate Access: It is essential to only give users the required access only for their required tasks. Giving them additional data access may lead to security risks for your database.
- Use Windows Login when Possible: If your companies or organizations use Windows accounts, use Windows Authentication for SQL Server logins. It’s a more secure and easier way to manage all the things going on in the system.
- Check User Permissions Regularly: For security purposes, please regularly check user database access. You can remove access for those non-users to keep things secure.
- Don’t Share Logins: Each person who uses SQL Server should have their own login. Hence, sharing logins makes it hard to check user activity.
- Use Strong Passwords: For a safe & secure database, users need to protect it with a strong and hard-to-guess password. This thing will keep your server safe from hackers or unauthorized access.
- Separate Duties: It is essential to make sure that people have specific server duties to guarantee that everything runs smoothly and efficiently without any trouble.
- Keep Everything Updated: Keeping your SQL Server database up to date is another best practice for SQL Server user mapping. Having up-to-date software enables you to fix bugs and security issues with total comfort.
- Keep Good Records: It is crucial for database administrators to keep a user access record in the SQL Server database. This will help you to keep track of all the things and you can easily fix the problems that come up.
By following the above-mentioned best practices, the user can easily manage user mapping in SQL Server. With this, you get the information about “How to get user mapping in SQL Server”.
Wrapping Up
In this technical blog, we discussed the most frequently asked user query “How to do user mapping in SQL Server.” Additionally, we covered all the things related to user mapping such as – what is user mapping in SQL Server, how it works, and what the best practices are. By following all these best practices of user mapping in SQL Server, users can ensure smooth user management and safeguard database integrity.